Why your employees can actually be the biggest risk to your business' security
Author: Laurence Glen | Date published: October, 16, 2023, UK | Read est: 11 min read
In an era where ones and zeros reign supreme, the greatest threats to your company's cyber security often walk on two legs, rather than appearing in lines of code. Yes, you guessed it - we're talking about your employees. While it might sound like the opening line of a cyber security-themed comedy, the reality is no laughing matter. The top-line statistics paint a stark picture: with 3.4 billion phishing emails sent every day, the biggest risks to your business's security are actually on the payroll.
So, why is this? Well, as the world's offices migrated to kitchen tables and coffee shops, the digital battlegrounds expanded. With a few clicks and a deceptive email, cybercriminals can strike from anywhere. In many ways, it made infiltrating larger companies, who had previously had robust cyber security, much, much easier. Seemingly innocuous links within emails can lead to personal bank information, sensitive company information and, in extreme cases, large sums of money being taken.
The rise in remote work has been paralleled by a troubling surge in phishing attacks since 2020, a type of threat that is often dismissed as easy to recognise, and yet can cause a litany of problems for businesses, especially if it is occurring regularly. In a government study of cyber attacks in 2022/23, they found that phishing was the most prevalent form of attack, with 79% of the businesses reporting some form of phishing breach or attack in the last 12 months.
That is why we have decided to delve into a study of our own, to showcase just how easy it is to fall for one of these emails, and, equally, just how easy it is to prevent, as long as you have the right cyber security awareness. And don’t be fooled: it isn't just fresh-faced recruits who fall prey to phishing lures. Even the most seasoned employees can sometimes let their guard down. It's human nature, after all. As the world grows more complex, so do the tricks up the cybercriminals' sleeves. But why focus on phishing when other threats lurk in the digital shadows? The answer is simple: data. Phishing attacks have left a trail of evidence that allows us to dissect and understand the anatomy of these attacks better than most other threats.
What is a phishing email?
What exactly is a phishing email? Well, imagine you receive an email that looks like it's from your bank, your boss, or even your favourite online store. It's got logos, fonts, and an urgency that just screams, "Click me!" The catch? It's not who you think it is. It's a phishing email - a deceitful, digital doppelgänger designed to lure you into a trap.
But why do people send these seemingly malicious missives? Well, 9 times out of 10, it’s for financial gains. Phishing emails are the cybercriminal's fishing line, cast into the vast digital ocean, hoping to reel in your sensitive information. They want your bank details, your login credentials, or anything else they can monetise. It's like catfishing for cash, and it's alarmingly common.
You might wonder if big companies, with their vast resources, are immune to these cyber scams. Quite the opposite! Even tech giants and Fortune 500 companies have been humbled by phishing attacks. It's like watching a superhero get tripped up by a banana peel - embarrassing but all too real. The list of companies that have fallen victim to phishing attacks reads like a who's who of the corporate world, from Apple to Google and beyond. Alternatively, if you’re thinking that you’re just a small fish in a big pond, and that no scammer would bother trying to catch, you would be mistaken. Attacks aren't always motivated by the financial ranking of a business: it's also the data they hold, connections they have to larger networks and supply chains. So regardless of business size or sector, you can be a target for cybercriminals.
In the following article, we'll delve deeper into the insidious world of phishing, taking a detailed look into the most successful phishing emails, the impact that training can have, and the steps we take to protect you from this all-too-common threat.
Common examples of phishing emails
As a part of Focus Group’s Security Awareness Training and Testing (SATT) service, we send out a variety of simulated phishing emails that are specifically aimed at catching employees out. No, not because we’re evil: we’re trying to get your employees in the habit of recognising a fraudulent message, and to avoid the fateful click that could mean the sharing of personal information. Below you’ll see some of our most successful sends, and why they are so effective at pulling the wool over your eyes:
‘Your teammates are trying to reach you’
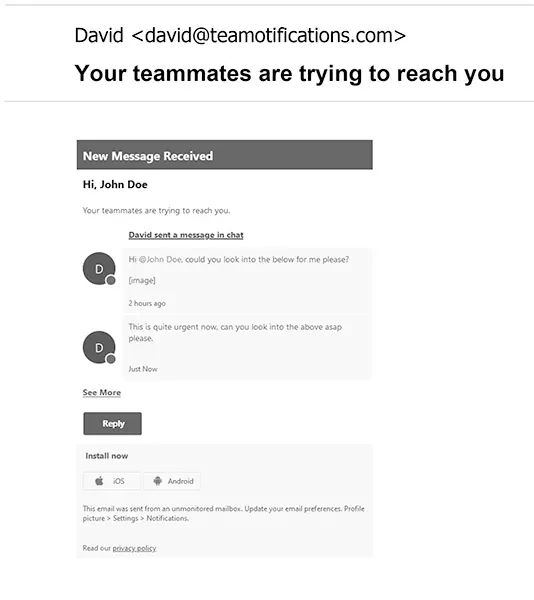
- Effectiveness: This phishing email boasts an impressive 90% open rate and a whopping 74% click rate. Why? Because it preys on our innate desire for teamwork and collaboration.
- Techniques: These emails often mimic internal communication tools or team messaging platforms. They play on that fear of missing out on important updates or messages from colleagues, compelling you to click on seemingly benign links.
'Rewards & Recognition Program'
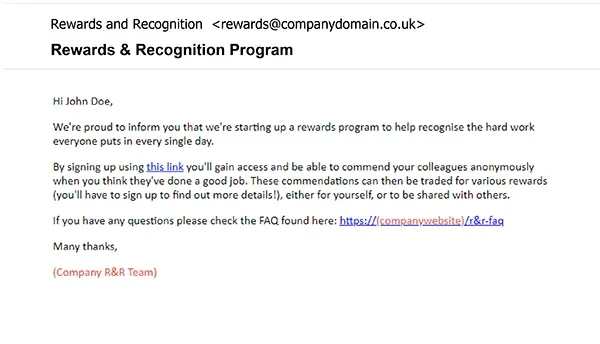
- Effectiveness: With a 68% open rate and a 58% click rate, this phishing email taps into that little part inside of us that believes we’re going to be employee of the month (or something of the sort).
- Techniques: These emails promise enticing rewards, bonuses, or promotions. They might claim you've won something or that you're eligible for special recognition. Temptation is their tool.
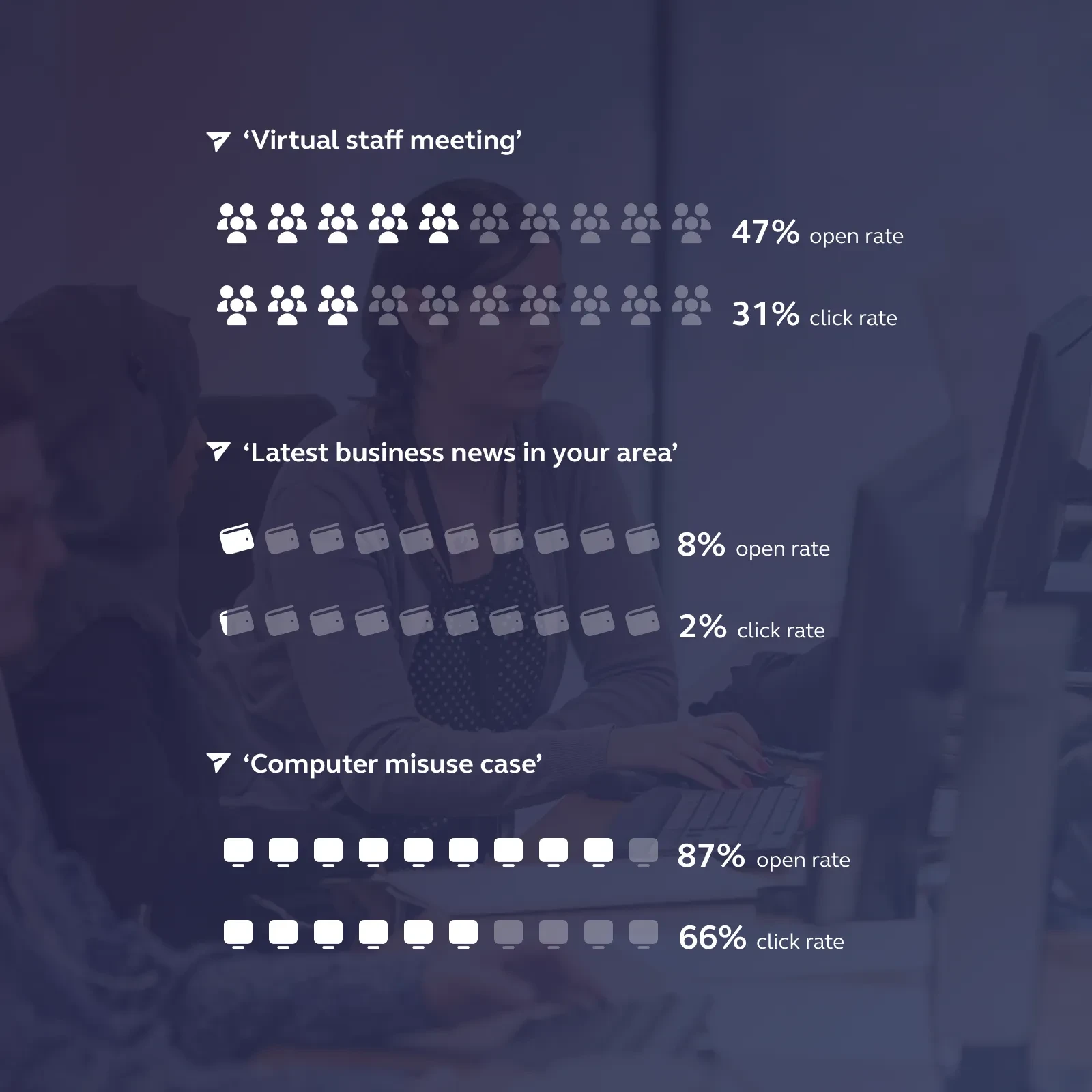
'Virtual Staff Meeting'
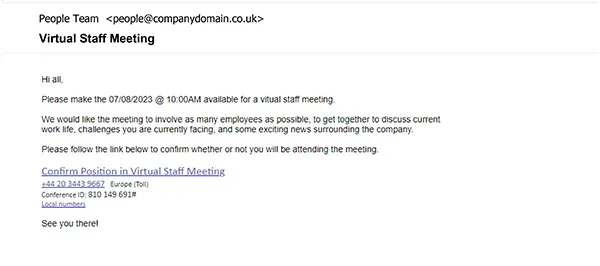
- Effectiveness: A 47% open rate and a 31% click rate make this phishing email a formidable threat. In an era of remote work, virtual meetings are the norm, and this email exploits that familiarity.
- Techniques: The email may mimic the format and language of legitimate meeting invitations, complete with fake details about an upcoming virtual gathering. Often, these emails will find you early in the morning, when your brain hasn’t quite switched on yet.
'Computer Misuse Case'
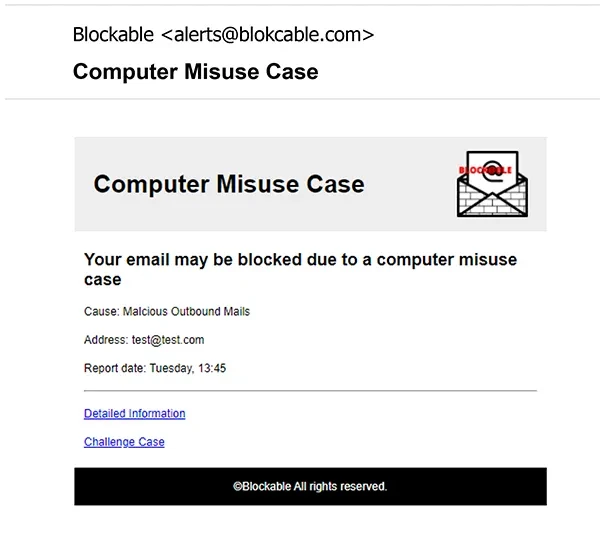
- Effectiveness: This phishing email boasts an impressive 87% open rate and a 66% click rate. Fear of legal consequences can be a powerful motivator.
- Techniques: These emails often masquerade as official notices from law enforcement or legal authorities. They claim your computer has been involved in a crime or breach, creating a sense of urgency and anxiety.
Our fake emails mimic the ingenuity of cybercriminals who tailor their tactics to prey on our psychology, curiosity, and vulnerabilities. Remember, the success of phishing emails lies in their ability to appear genuine and exploit human tendencies. Vigilance, critical thinking, and cyber security awareness are your best defences against these digital decoys.
The 2023 Focus Group phishing statistics
As part of our own study, we took a sample of 20,000 emails, sent out over the course of a year, to a variety of employees across different industries. Every one of these signed up for our service, and received continuous training to try and avoid the possibility of a breach. Sent out at random times in the month, at all kinds of hours, we make sure that there is no pattern to our testing, to ensure the most realistic experience for everyone involved in our course. In this way, you can see throughout this study that over just a short period of time, the number of employees clicking on these malicious emails reduces to almost none. Of course, the ultimate aim is to get that number to zero, however when you see the difference between pre and post training, you’ll be amazed at the impact it has on people’s awareness.
The concerning baseline
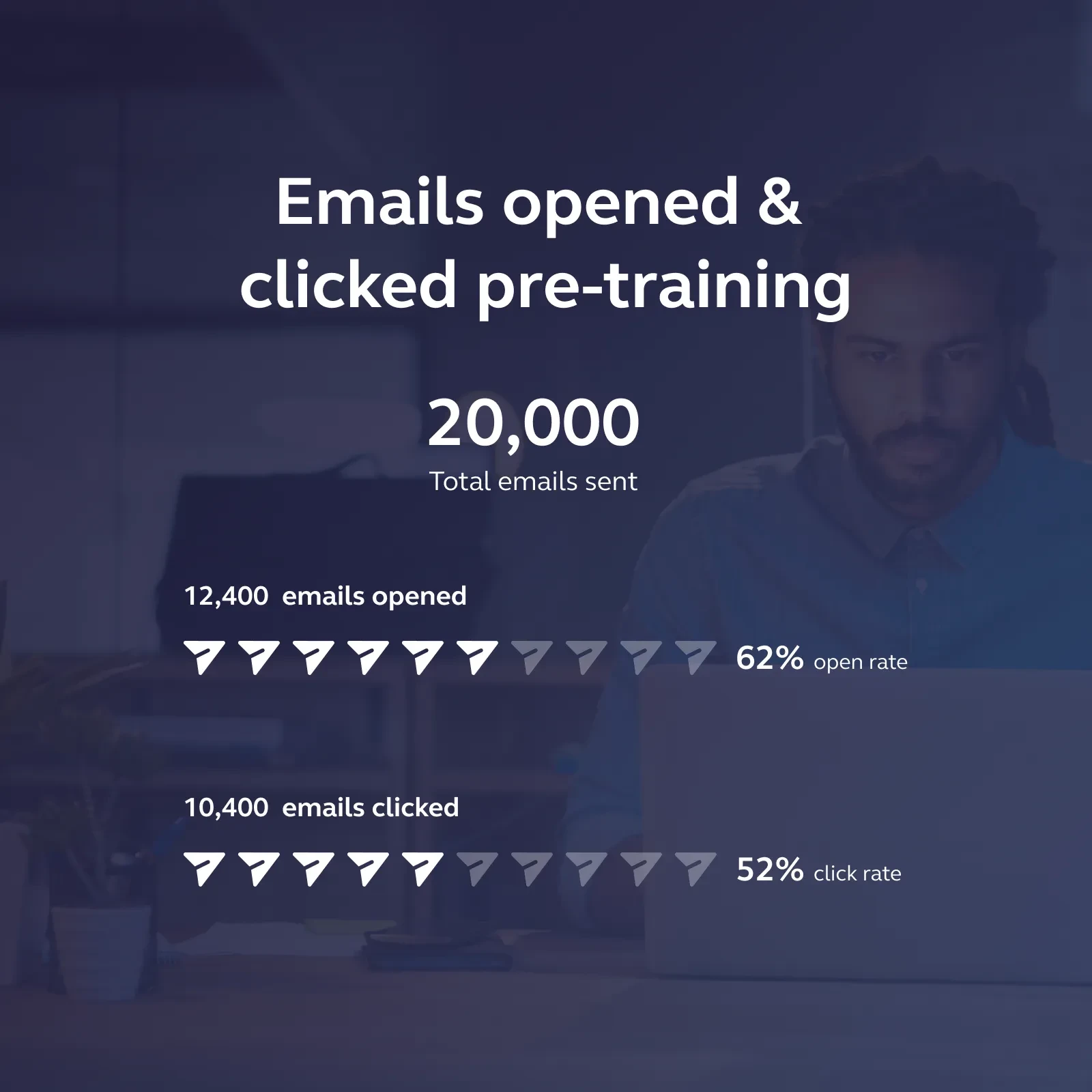
When your employees aren’t trained properly, they don’t expect a threat. Especially one that comes in through their email. But that is exactly how most cyber breaches happen: and the numbers from our own study have shown the truth of that fact. With 52% of employees clicking on the dangerous links within the emails, it’s clear that security is at the very back of their minds.

The incredible part is that this goes out to all types of employees: from sales personnel all the way up to managers and directors. Which means that, although the fallout of a lower-level employee clicking on these links might be minimal, the impact of a higher-level employee clicking on it could be catastrophic. Not just for the leaking of information or personal details, but for employee and client confidence. Most people see themselves as just a cog in the larger wheel of a company, but when that cog breaks, it can expose the inner workings to even more threats.
The comparison

Post training, the numbers tell a very different story. Although nearly the same number of people click on the email initially (52%) this is where their expert training kicks in. Like hardened marines, their danger senses start tingling, and they quickly realise that something is amiss. This is why, post-training, the number of clicks on the dangerous link reduces to just 4%. Four percent. And that is just with one round of training.
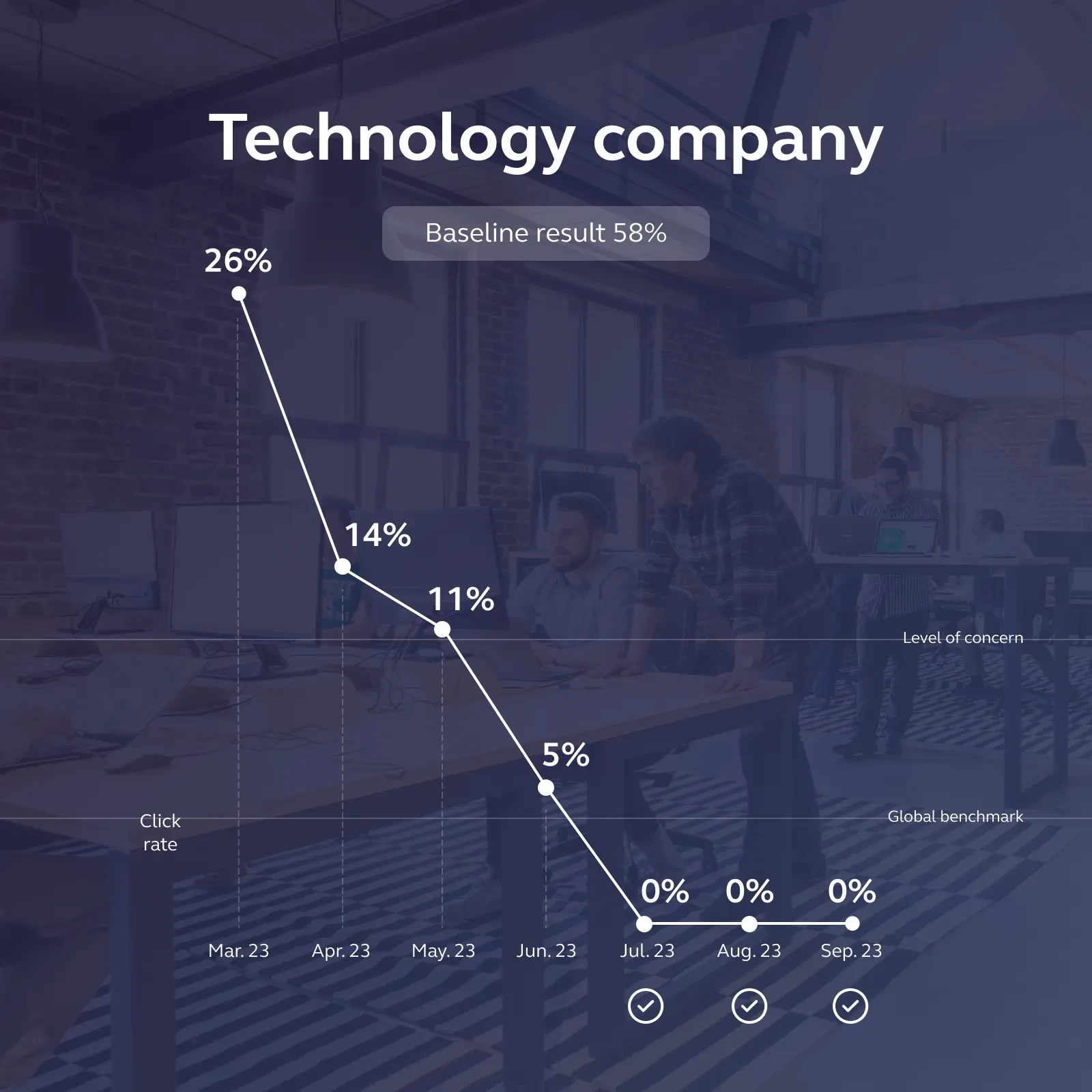
As more and more people get trained, the number reduces further and further, with our average monthly click rate now sitting at 1.3%. This is thanks to our no-nonsense attitude to a fake phishing email click. Every time an employee clicks on one of our enticing emails, they have to go back in for training. Every. Single. Time. So eventually, the threat of having to do the training sits on par with the worry about giving away all your personal details.

What do our experts think about phishing emails?
So by now, you’ve realised that the threat is real. You can see how many people, pre-training, get caught by this type of scam. But you might still be thinking: this isn’t that much of a problem for me. Well, we spoke to one of our experts in the cyber security department to really hammer it home that this is something that any business owner needs to be aware of.
What part of the training are people most interested in?
The interactive quiz elements around the ‘Real or Phishing’ questions where users are expected to interrogate the emails and hover over the elements are always well received. The recent switch to modular training allowing clients to customise their course with modules relevant to them is popular as well.
What types of emails are people caught out by the most?
Typically the internally targeted templates appearing to come from trusted colleagues score well as they play on things like a recognised name and company logos/signatures to gain the trust of the user.
Are employees surprised when they click on fake emails?
Of course! Those who click are usually expecting a reward or something that was promised in the email so being met with an ‘Oops you clicked…’ page is the last thing they were expecting. Most also don’t realise how easy it is and think it will never be them.
How does phishing testing and training compare to other areas of cyber security?
Phishing testing and training focuses more on the human element of cyber security, admitting that the security of the company is only as strong as the people that work there.
When do you need to be most alert for phishing emails?
People tend to be more susceptible to these types of scams during times of hardship or during the holiday season where money may be stretched and something promising an easy way out or helping hand can be too tempting. However, there are always going to be phishing attempts going round so there is no real best time to look out for them. The better approach is to adopt the skills needed to spot them into a habit.
Is it newer or seasoned employees that get caught out the most?
A mix of both, new starters who may not be used to company systems or colleagues’ wording may be more likely to fall for an attack but on the other side you have long standing employees who may become complacent and overlook the mistakes in the emails.
Safeguarding your business in a digital world
In the ever-evolving landscape of cyber security, where the line between safety and vulnerability is razor-thin, it's crucial to acknowledge that your employees can be both your first line of defence and your most significant liability. As we've explored in this journey through the realms of cyber threats, phishing emails, and their impact on your business, it's abundantly clear that awareness, education, and ongoing vigilance are your best allies.
So, how do you prevent cyber attacks caused by employees?
At Focus Group, we understand that combating cyber threats begins with understanding your current risk level. That's why we start with a baseline phishing test, a simulated phishing attack that targets everyone in your business. This initial step provides us with valuable insights into your organisation's vulnerability, often revealing that 40 to 70% of employees unknowingly put security at risk. Our objective at this stage is to assess and benchmark your company's cybersecurity posture.
The Step-by-Step Action:
Stage 1 - Baseline Assessment:
- Begin with a targeted simulated phishing attack.
- Analyse the results to establish your current risk level.
- Use this baseline as a reference point for future assessments.
Stage 2 - Education and Training:
- Provide extensive online courses covering a wide range of cyber security topics.
- Ensure staff understands cyber risks and how to identify and prevent attacks.
- Offer deeper dive courses for at-risk employees or those requiring advanced training.
Stage 3 - Ongoing Vigilance:
- Implement monthly phishing tests tailored to your business.
- Test employees' vigilance and reinforce their training.
- Enrol employees in additional training if they fall prey to simulated phishing attacks.
- Aim for a 0% click rate to maintain optimal security.
Taking charge of your security
In the ever-evolving world of cyber threats, staying one step ahead is imperative. Cybercriminals become smarter with each passing year, adapting their tactics to bypass defences. Therefore, the commitment to cyber security is never complete. It's a continuous journey, one that requires dedication, training, and a proactive stance.
At Focus Group, we're here to guide you through this journey, helping your employees become the strongest link in your security chain. By combining baseline assessments, comprehensive training, and ongoing vigilance, we create a culture of cyber security that not only safeguards your business but also empowers your employees to be the first line of defence against threats. Together, we can ensure that your digital kingdom remains secure in an ever-changing landscape.

Laurence Glen
IT Director
Our IT world, together with the ongoing development of this business-critical portfolio of services, is in very capable hands with Laurence at the helm. IBM-trained and with a 22-year track record of proven success in the IT sector ensures Laurence is perfectly placed to lead the overall IT strategy for Focus Group, ensuring we’re at the forefront of product development and service innovations in order to deliver the best possible IT technologies for our customers.